Why Did I Open a Malware Research Channel
One day I was sitting, looking at my screen trying to solve a problem. I was stuck and I knew I was not the only one who had this problem.
As a malware researcher what were my options to seek help? Twitter? I felt like it was too public, and the trolls will kill any useful discussion. StackOverflow? Maybe, but it’s more suitable for precise questions or a reversing problem.
So, I started to ask around if there are any communities I can join to share my frustration with others.
any cool recommended infosec slack channels ?
— Omri Moyal (@GelosSnake) September 25, 2017
I got a few invites for Infosec related groups, some owned by businesses and others which were pretty much dead. None were dedicated to malware research. I felt I really needed a community of malware researchers to share the pain, elaborate on Intel, ask questions and work together on malware outbreaks. So instead of waiting around to either find one or hoping someone else will create it, I decided not to waste time and just make it happen.
I searched around for the best platform to run this kind of community. IRC, like your first love, was the first platform I thought about, but quite early it was clear it wasn’t going to work. There was also an option to use a web forum, but like IRC, it felt outdated and required too much maintenance. Telegram was also an option but with the number of topics discussed in such group a more flexible platform was needed. So, I turned to Slack. Being built to replace email and improve communication in the workplace, it felt like the right platform to start with. Also, a lot of malware researchers were already on Slack due to their internal work channels, which made it very easy to connect.
Opened dedicated @SlackHQ for Malware Research, feel free to PM for an invite.https://t.co/GPZHhDP6fk
— Omri Moyal (@GelosSnake) September 26, 2017
The reaction was pretty clear. My gut feeling was correct and I was not the only one seeking this kind of group and community.
I did not expect the group to grow so fast and luckily my partner in (cyber ;) ) crime @DamskyIrena accepted my request to help manage the channel and inspect incoming invites.
#####What happens in the group?
Mainly, it’s a place for like-minded malware researchers to ask questions, share intel, IOCs, learn from each other, promote their research and have fun.
The channel is divided into different rooms like general, exploits, tools, automation, news, help, etc. We have dedicated rooms for specific malware like emotet or outbreaks, and even places for conferences and events where people can easily schedule meetings and drink nights.
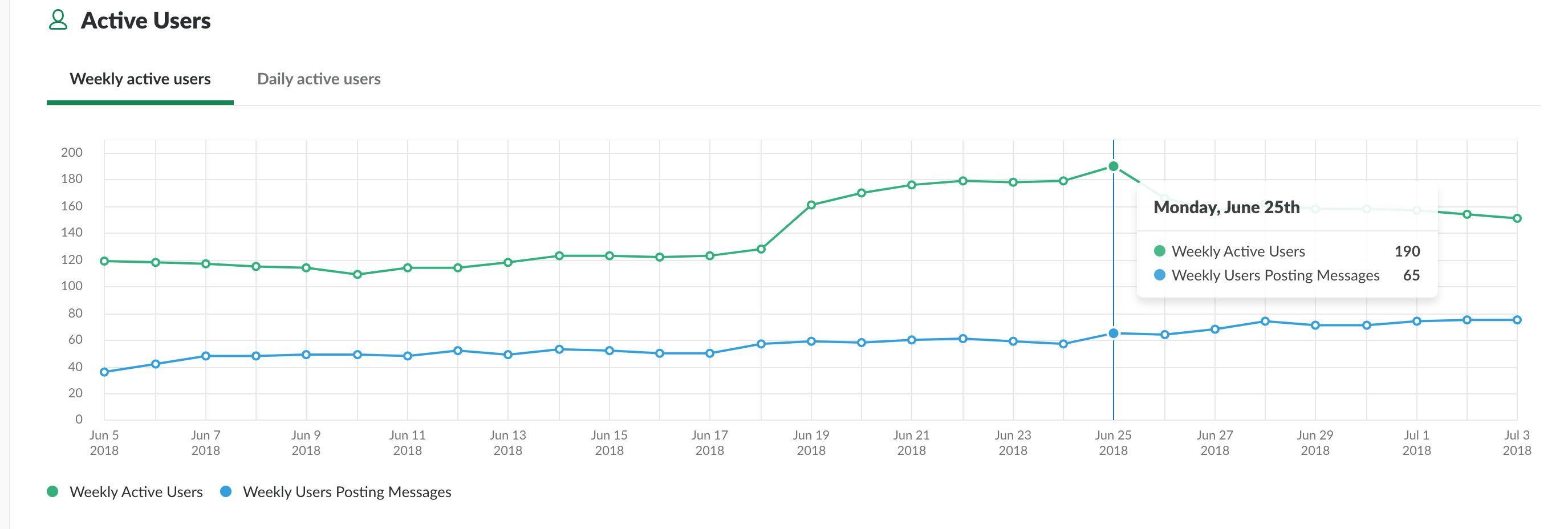
The group has over 380 registered members, around 180 active monthly members and 45k messages sent, not to mention the amount of signatures, IOCs and rich content produced from the communications in the group.
To get a better overview of the channel, I’ve asked other members to give their own opinion:
this is an interesting and useful group to be in. I’m in many slack communities that cover lots of different subjects around information security, but this is the only one focused specifically on malware research. I’ve found it to be fairly active but not noisy. The participants seem to range in background and knowledge, and that seems to lend to a collaborative feel to the overall community. People can ask questions - literally any question - regarding malware or research, and people will respond with useful insights. People here generally seem to have a good sense of humor which is also highly important if you ask me. I love that there are some really sharp people here that don’t mind answering questions or helping out. I’m happy I joined and happy to be around in this particular slack.
Over the past two years I’ve been actively joining Slack, and Discord groups focused on cyber-threat related tracking and awareness. Upon joining the MalwareResearch Slack group, it quickly became one of the more productive collaborative mediums for research and information sharing. From having a large membership of extremely talented people from across all kinds of different and unique industries or focus to expanding beyond just “malware” research into exploitation, meet-ups, jobs, OS based discussions, and many more topics. It has grown into a community of its own who are all willing to help each other out without any expectations.
As a solo/hobby researcher, I find this slack is the best place I can go to meet other researchers who have far more real experience than me, and I’ve made far more connections here than I could have dreamed of before I landed an invite. Malware analysis is a bit of a passion for me and I’m hoping to relocate next year and look for a research role and being here this year has helped me grow to a place where I feel I have the experience I would need to do this as a real job. It’s also helped me get in contact with people working on the same malware as me and share our findings with each other which has been awesome.
The malware research group is a powerful resource for malware researchers or anyone that wants to upgrade their skills. With over 200+ members across the globe, it has specialists from all vendor companies including members of certs that can help on several fronts. You can share and ingest IOCs and comes especially handy when a zero-day vulnerability is noted. As the latest threat is being spoken about among business circles, the group will bring out the latest intel on that front - linking emerging information, pocs, and even the newest detection signatures. You can share and receive regexes, snort, and Yara rules. Working on a project? Asking in the separate chat channels can link you with people interested in helping. Got a question on reversing that you want help on? Want to connect with others that focus on your threat area? All of which can be found and utilized by the members. You can also share files instantly through slack, link script snippets, snapshots, and start group conversations. I’ve personally used it to share intel, help others where I can, and provided intel from the team to the business I work with (threat intel and vulnerability teams that are eager to obtain info). In the past year I’ve made connections with new researchers I wouldn’t usually meet and also have held controversial discussions on subjects bringing in input from others. I find it to be a phenomenal resource that I will utilize further when my own malware reversing skills get up to par.
For a long time, I’ve been looking for a place to discuss malware research-related matters, as well as get acquainted with like-minded InfoSec pros. Needless to say that it’s difficult to find out in the open, without the hazard of being exposed to people who bring wrong intentions or just bad vibes. I got introduced to the group by @DamskyIrena, who recognized this need and the ability of this Slack space to provide it. Ever since I joined, I had the privilege of meeting some of the best professionals in our industry and share views on a wealth of matters tackled during my work or personal endeavors. I met a warm and inviting community, people who help one another, share tips and tricks and made our field a truly great place to be.
#####How can you join?
To join the group all that needs to be done is to fill up the form here. The group admins will view your request, and a slack invite will be sent. (Since we are manually verifying each and every request, it might take us a few days, if you feel we haven’t addressed your request - you can ping me or @DamskyIrena on twitter)
We are welcome new members willing to take part in this great community.